Gamify Your Product Security Maturity
Make Security a Team Sport—Drive Adoption, Engagement & Execution, Not Just Alerts
Traditional tools track security issues—Start Left® ensures they get fixed. But security success requires more than tools; it’s about culture. Start Left® embeds real-time training, incentivizes best practices, and empowers Security Champions to lead security adoption—transforming security from a reactive burden into seamless execution.

Motivate & Reward Secure Development
Incentivize security best practices with challenges, leaderboards, and rewards.
Make Training Seamless
Embed security training directly into engineering workflows for real-time learning.
Security Adoption Fails Without Engagement—We Fix That
Start Left® reinforces security best practices through real-time feedback, skill-based progression, and competitive incentives. Its gamification that drives real security adoption.
Monitor adoption and maturity with performance insights.
✅
Security Challenges & Leaderboards –
Recognize top-performing developers.
✅ Just-in-Time Training & Coaching –
Deliver targeted learning when it matters.
✅ Adaptive Levels –
Reward developers for progress in secure coding maturity.
✅ Team-Based Security Metrics –
Track adoption and performance across teams.

Security Champions: Build a Security-First Culture
Security isn’t just a function of the security team—it’s a shared responsibility across engineering. Start Left® enables organizations to identify, train, and reward Security Champions who drive security culture at the team level.
✅
Recognize Security Champions –
Reward developers who lead security initiatives.
✅ Build Security Ownership at the Team Level –
Empower engineers to take responsibility for security adoption.
✅ Provide Leadership Visibility –
Showcase Security Champions' impact on engineering performance.
✅ Connect to Developer Performance Insights –
Link gamified security efforts with broader
Optimize Developer Performance insights.
Move Beyond Static Security Training—Make Learning Engaging & Actionable
Traditional security training doesn’t scale, isn’t engaging, and is rarely retained. Start Left integrates real-time, gamified upskilling into developer workflows to ensure security becomes second nature.
✅
Just-in-Time Training –
Personalized lessons based on actual developer activity.
✅ Progression & Badges –
Encourage growth with learning paths & achievements.
✅ Real-World Security Labs –
Gamified scenarios enhance developer awareness.
✅ Coaching & Feedback Loops –
Reinforce knowledge with actionable insights.

Security Program Gamification
Optimized for DevSecOps
Risk Assurance Score
Instantly see performance with AI guidance that pinpoints critical areas for security improvements.
Security Training
Prescribes personalized and situational secure code training to specific developers creating risks.
Threat Detection
Analyze and correlate data that detects people, activity, process, and tech risks that scanners miss.
Security Posture Management
Uncovers risks across teams, skills, code, CI/CD, containers, and IaC, ensuring comprehensive coverage.
Auomated Prioritization
Generate SBOMs and monitor code for known vulnerabilities and CVEs, prioritized by exploitability.
Policy-Driven Guardrails
Checks, enforces, tracks, and validates adherence or violations to SLAs, best practices, and policies.
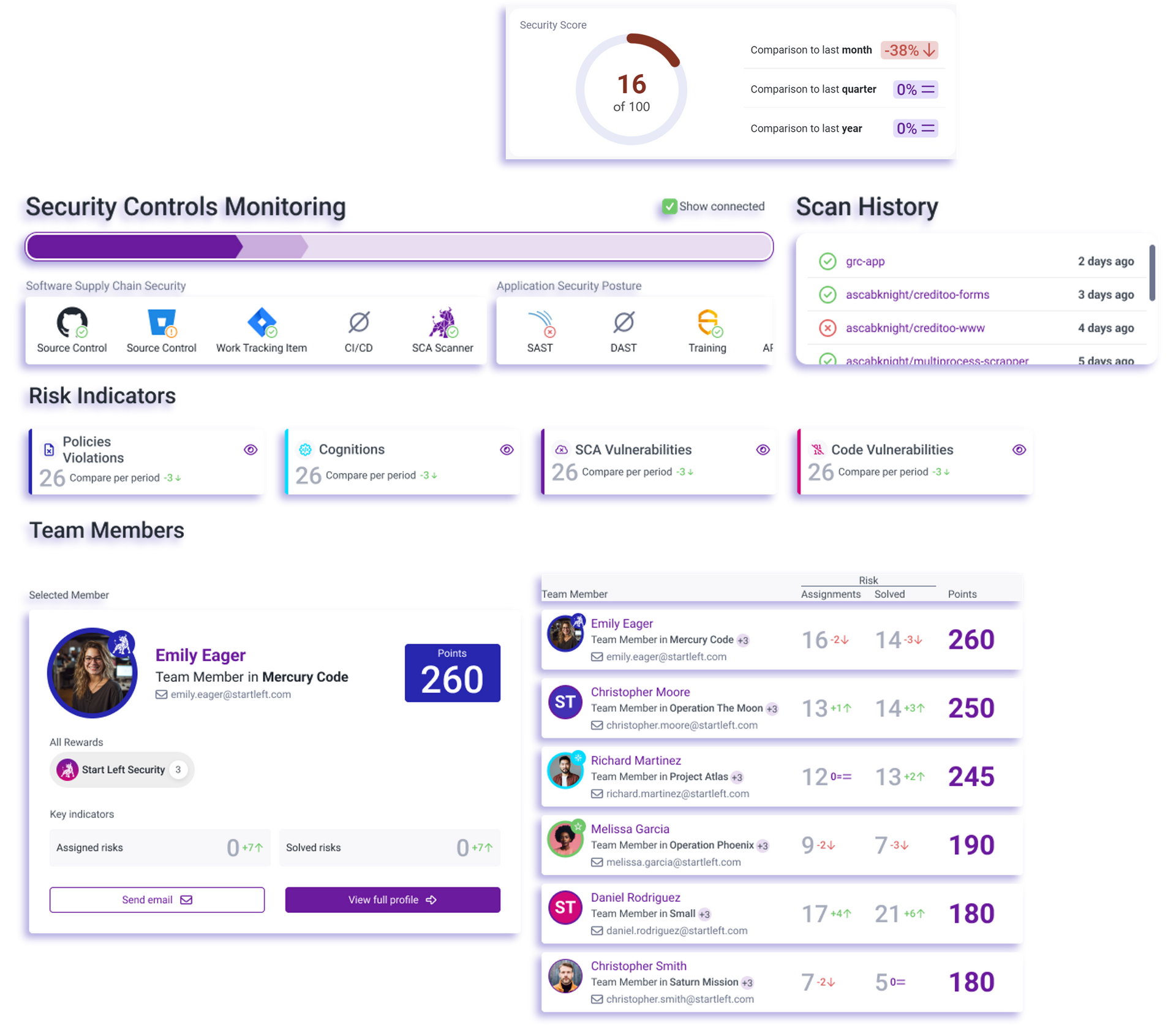
Measure & Improve Security Execution
Track Adoption, Progress & Risk Reduction in Real Time
Security improvement shouldn’t be anecdotal—Start Left provides measurable security execution insights.
✅
Live Security Maturity Scoring –
Track adoption and improvement across teams.
✅ Security Performance Dashboards –
Show leadership how security impacts engineering execution.
✅ Engagement Metrics & Developer Insights –
See who is leading security adoption—and who needs help.
✅ Connected to
Developer Performance Optimization –
Link security adoption to broader engineering.
With Start Left®'s "Manage Your Security Program" use case we're able to unlock unmatched value with their posture management capability. From early programs to enterprise programs, Start Left® empowers organizations to achieve optimal efficiency. Our clients are able to discover and map data flows, automate security efforts, maximize limited resources, and constantly evaluate program performance.
Security success isn’t about policies—it’s about execution.
Ready to make it measurable?
Get a demo
Ready to make it measurable?













