Replace AppSec Tools
Ditch the Legacy Tools & Eliminate Siloed Risk: One Unified Platform for Security & Execution
Traditional application security tools are expensive, fragmented, and hard to manage. They create siloed risk, redundant workflows, and leave teams in the dark. Start Left® consolidates security testing, execution intelligence, and risk management into one unified platform—giving teams full visibility, automation, and control.

Eliminate Tool Sprawl
Replace redundant security solutions with an all-in-one execution platform.
Automate Security Testing
Embed risk detection into every stage of development.
Traditional AppSec Fails: Siloed Risk, Expensive, Complex & No Execution
AppSec tools create more problems than they solve. Start Left® replaces fragmented security solutions with an execution-driven approach that eliminates complexity and inefficiency.
All the Capabilities You Need—In One Place for Execution-Driven Security
Start Left® unifies security posture management, risk prioritization, and built-in security testing to provide an actionable, real-time security execution framework.
Risk Assurance Score
Instantly see performance with AI guidance that pinpoints critical areas for security improvements.
Security Training
Prescribes personalized and situational secure code training to specific developers creating risks.
Threat Detection
Analyze and correlate data that detects people, activity, process, and tech risks that scanners miss.
Security Posture Management
Uncovers risks across teams, skills, code, CI/CD, containers, and IaC, ensuring comprehensive coverage.
Auomated Prioritization
Generate SBOMs and monitor code for known vulnerabilities and CVEs, prioritized by exploitability.
Policy-Driven Guardrails
Checks, enforces, tracks, and validates adherence or violations to SLAs, best practices, and policies.
Built-In Security Testing That's
Embedded, Not Bolted On
Open Source License Scanning
Track license risks like hidden obligations and non-compliance, while guardrails ensures only approved OSS is used in projects.
Open Source Dependency Scanning (SCA)
Generate SBOMs and monitor code for known vulnerabilities and CVEs, prioritized by exploitability.
Secrets Detection
Checks and validates exposed API keys, passwords, certificates, and encryption keys in dev workflows.
Static Code Analysis (SAST)
Finds OWASP Top 10 issues, prioritizes them, and suggests AI-powered code fixes for developers.
Container Image Scanning
Scans for vulnerabilities, generates SBOMs, and prioritizes risks for secure, compliant deployments.
Surface Monitoring (DAST)
Scan web apps for vulnerabilities using simulated attacks. Built on ZAP, or integrate your own tool.
Infrastructure as Code (IaC) Scanning
Scans Terraform & Kubernetes for misconfigurations and risks, ensuring secure, compliant infrastructure deployment.
Code Rot / End-of-Life
Identify outdated frameworks and applications that are no longer maintained to prevent software decay and ensure product stability.
Connect Your Other Tools
Integrate any tool with Start Left® to correlate, assign responsibility, triage, and automatically prioritize findings across your existing stack.
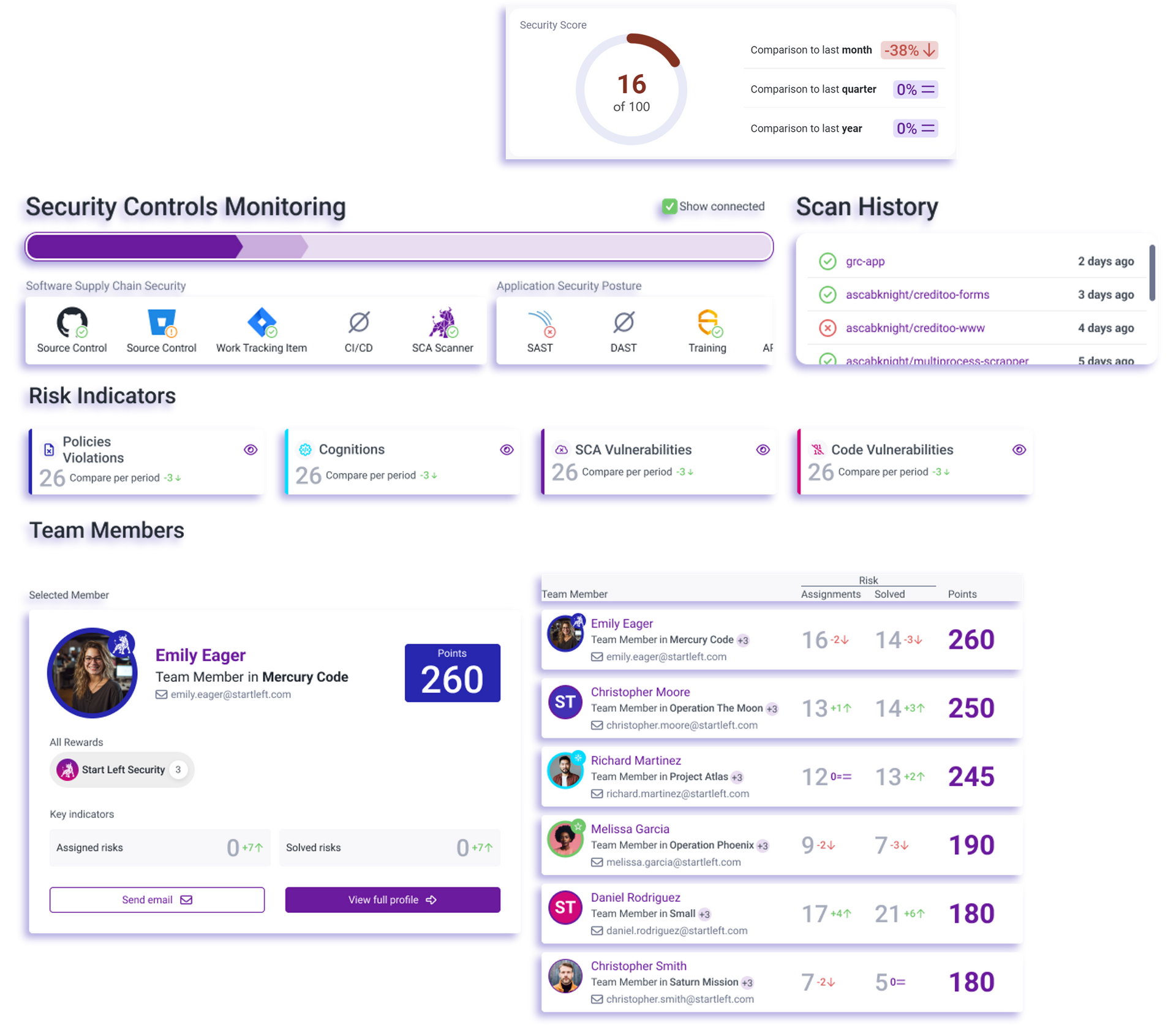
From Posture to Progress:
Make Security Adoption Seamless
Tracking security posture is just the beginning—real security happens when teams adopt and execute security best practices at every stage of development.
✅ Security Scores & Analytics – Measure team performance and prioritize the highest-impact risks.
✅ Integrated Security Testing – Detect vulnerabilities with pre-runtime testing and continuous monitoring built into DevOps workflows.
✅ Automated Prioritization & Policies – Enforce security SLAs, best practices, and risk-based prioritization (CISA KEV, EPSS).
✅ Seamless Execution – Automate workflows, streamline remediation, and connect with any security tool.






