Start Left® Security's Risk-Based Vulnerability Management Use Case:
Product-Centric Secure Code & CI/CD Pipelines
Streamline vulnerability management and contextual insights with Start Left®'s patented Risk Model, the industry's first "Product Integrated Risk Analytics & Threat Evaluation" integration methodology, "PIRATE®". PIRATE® automates product-centric views of developer-specific vulnerabilities, enabling targeted prioritization and remediation. Enhance collaboration and get faster security.
The Challenge of Vulnerability Management Without Context.
Vulnerability management poses a significant challenge in ensuring robust application security postures. The lack of context, such as the product, CI/CD pipeline, dynamic SBOMs, and developer team members involved, hinders the effective identification and remediation of vulnerabilities.
Without product context, vulnerability management efforts are fragmented and disconnected. Security struggles to prioritize risks based on their potential impact, leading to inefficient resource allocation and delayed remediation. Moreover, without understanding the specific compensating controls and development practices, it becomes difficult to tailor mitigation and engage with developers, product owners, or operations, resulting in delayed response times. This fragmented approach increases risk sand decreases the overall effectiveness of security.
Challenges Solved
Integrated security into contextual CI/CD pipelines
For DevSecOps risk governance and vulnerability management performance monitoring, integrate surveillance and discovery into every CI/CD pipeline.
Mapped security issues to specific teams
Get a handle on defects, drifts, risky changes, rogue development activities, controls, secrets, vulnerabilities, and configuration issues.
Contextualized product risks and threats
Integrate security analytics, behavior analytics, and compliance checks from code, people, processes, applications, and cloud platforms into every product team.
Get a demo!
Learn how Start Left® reduces blind spots and helps you gain control of vulnerability management in under half an hour.
Tell us a little about your organization and we'll connect you with an expert who can share Start Left®'s Platform and answer any questions you have.
Contact Us
Product Integrated Risk Analytics & Threat Evaluation
Unlock dynamic asset inventory and risk discovery with Start Left®'s
PIRATE® gives full situational awareness of risks on every product team. Automate PIRATE®'s data mining and reverse engineering tools. Guide teams with precision and speed to elevate your vulnerability management.
Best Practices Enforcement
Business Impact / Criticality Analysis
Risk Ownership & Contextual Controls
Developer Security Protection Baselines
Team Activity, Behavioral & Risk Performance Analysis
Continuous Team Risk & Threat Surveillance

Vulnerability Management Solved with Start Left® Security
Enhance collaboration and secure your cloud product postures by harnessing the power of automation and correlation of inline scanning for SCA, dynamic SBOM, AppSec tools, and more. With Start Left®, empower your DevOps, CloudOps, SecOps, and GRC teams for effective vulnerability risk management.
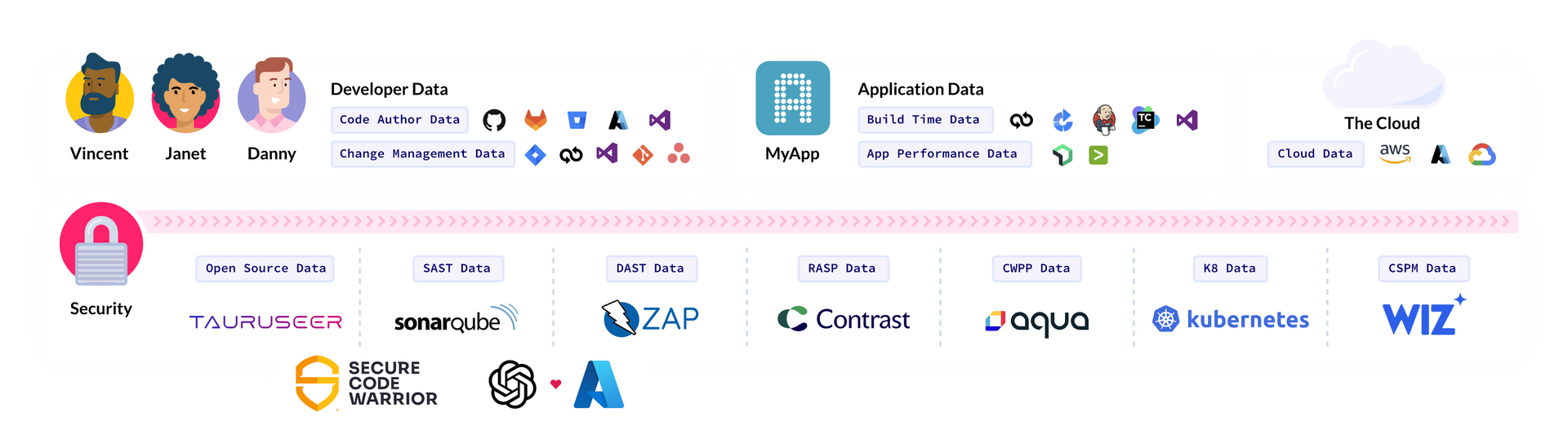
Team Security Baselines
Deploy analytics where the PIRATE® Risk Model learns each team's developers, tools used, controls configurations, source of code, and CI/CD integrity to flag risky changes of the trusted baseline for review & verification.
Build Process Hardening
Further operationalizing the Team Security Baselines and Dynamic SBOM capabilities via the PIRATE® Risk Model, Start Left® identifies potentially malicious code modifications and access to repos that may be insider threat.
AST Automation
Achieve comprehensive AST coverage from Day 1 with Start Left®'s out-of-the-box tools. Discover and eliminate tool coverage gaps for orchestration and automation. Get the full picture with automatic correlation of all vulnerability findings from all scanners.
Workflow Orchestration
Foster tighter collaboration between SecOps, DevOps, Engineering, & GRC with security workflow orchestration into the tools you already use like JIRA, Azure, ServiceNow, and more to speed response and track issues.
Intelligent Prioritization
Remove headaches of manual analysis and make it easy for your teams to take smart actions. With Start Left®, automate a special way to prioritize risks. It's called SHERPA™ (Shared Embedded Risk Prioritization Analytics). The first in the industry.
Continuous Assurance
Automate team-based analytical remediation verification: source code commits (Jenkins) to version control repository (GitHub) correlated to work item tracking (JIRA) with proprietary scanning to validate code fixes.
With Start Left®'s unique product-centric approach for managing vulnerabilities allowed us to evolve into an efficient Agile DevOps model and run an AppSec program effectively by allocating scarce resources to the products that matter most to the company. We can now stop searching for security holes and instead focus our efforts where they will have the greatest impact.
Connect and start reaping the benefits in no time.
Our no-code API makes it a breeze.
Get a demo
Our no-code API makes it a breeze.







