The Hidden Costs of Ignoring Security by Design
Security by Design Isn't Optional: Why Waiting Derails SaaS Growth Later
In today’s fast-paced digital world, speed to market often takes precedence over all else. But what happens when Security by Design is treated as an afterthought? The result is often a costly, time-consuming, and reputation-damaging awakening.
For any company that develops software as part of their revenue stream, embedding Security by Design (SBD) into the development process is no longer just a best practice—it’s a government-mandated requirement. Neglecting these principles can lead to cascading challenges that affect compliance, customer trust, and operational efficiency.
In this blog, we’ll explore the risks of neglecting Secure software development, highlight the costs of inaction, and explain how adopting Software security best practices can safeguard your organization.
The True Costs of Neglecting Security by Design
Failing to integrate Security by Design into your software development lifecycle (SDLC) creates vulnerabilities that are technical, operational, and reputational. Here’s what’s at stake:
1. Reputation Damage: A single data breach can irreparably tarnish your reputation, especially if you handle sensitive customer data.
Example: High-profile companies like Zoom faced public backlash when security flaws were exposed, requiring costly fixes to rebuild trust.
2. Revenue and Customer Loss: Enterprise customers demand secure software development practices. Without trust in your product, churn increases, and you lose deals to competitors with stronger security postures.
Cost: Losing even one enterprise customer could mean a significant revenue hit.
3. Regulatory Fines and Legal Costs: Organizations often underestimate their obligations under frameworks like GDPR, CCPA, and HIPAA.
Example: Non-compliance fines can reach up to 4% of global revenue, making neglect a crippling financial risk.
4. Escalating Technical Debt: Retrofitting security after deployment is exponentially more expensive than embedding Security by Design early.
Cost: Addressing vulnerabilities post-deployment can cost up to 30x more than resolving them during development.
5. Operational Inefficiencies: Without software security best practices, teams waste valuable time reacting to breaches instead of driving innovation.
Impact: Product delays, downtime, and missed opportunities for innovation and growth.
6. Competitive Disadvantage: Certifications like SOC 2 or ISO 27034 are often prerequisites for enterprise contracts.
Impact: Delays in achieving compliance due to poor Security in SDLC practices can cost you opportunities.
Building a Security by Design Foundation Early
Security by Design is not just about tools; it’s about embedding a culture of security within your teams, processes, and development cycles. Here are key principles for success:
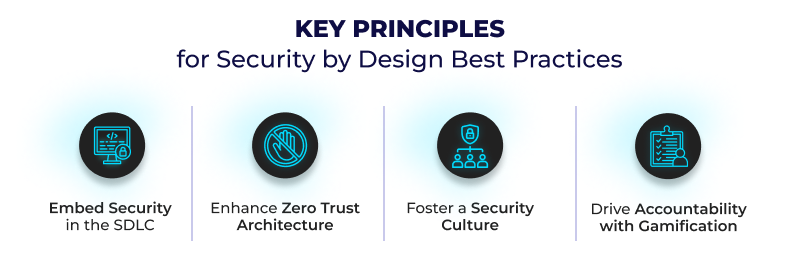
Embed Security in the SDLC: Integrate security at every stage of your software development lifecycle to ensure vulnerabilities are addressed proactively.
Enhance Risk Management: Adopt a risk-first approach to prioritize risk management in software development, enabling better decision-making and resource allocation.
Foster a Security-First Culture: Educate and empower your team to adopt a security-first mindset, making security everyone’s responsibility.
Drive Accountability with Gamification: Engage teams, foster accountability, and encourage proactive participation in activities like policy adherence, vulnerability management, and compliance tracking through rewards and recognition.
The Role of a Security by Design Enablement Platform
A comprehensive enablement platform should deliver seamless support across every aspect of your security operations:
- Provide Unified Visibility: Centralize your security posture, ensuring clear oversight across tools, teams, and processes.
- People-Centric Risk Management: Align security strategies with human behavior by tracking, managing, and mitigating human-related risks effectively.
- Automation Meets Accountability: Streamline policy enforcement, risk assessment, and vulnerability management while enhancing compliance and cross-team collaboration.
- Bridge Silos: Enable collaboration across developers, application security teams, and leadership to drive cohesive security strategies.
- Scalability: Scale effortlessly with your business, integrating new tools and leveraging real-time threat intelligence for continuous enhancement.
- Integrate Seamlessly: Ensure compatibility with a broad range of tools, including best-of-breed CI/CD platforms and open-source or commercial security scanners.
- Support Security Maturity: Align with a security maturity model to guide ongoing improvement and adapt to evolving needs.
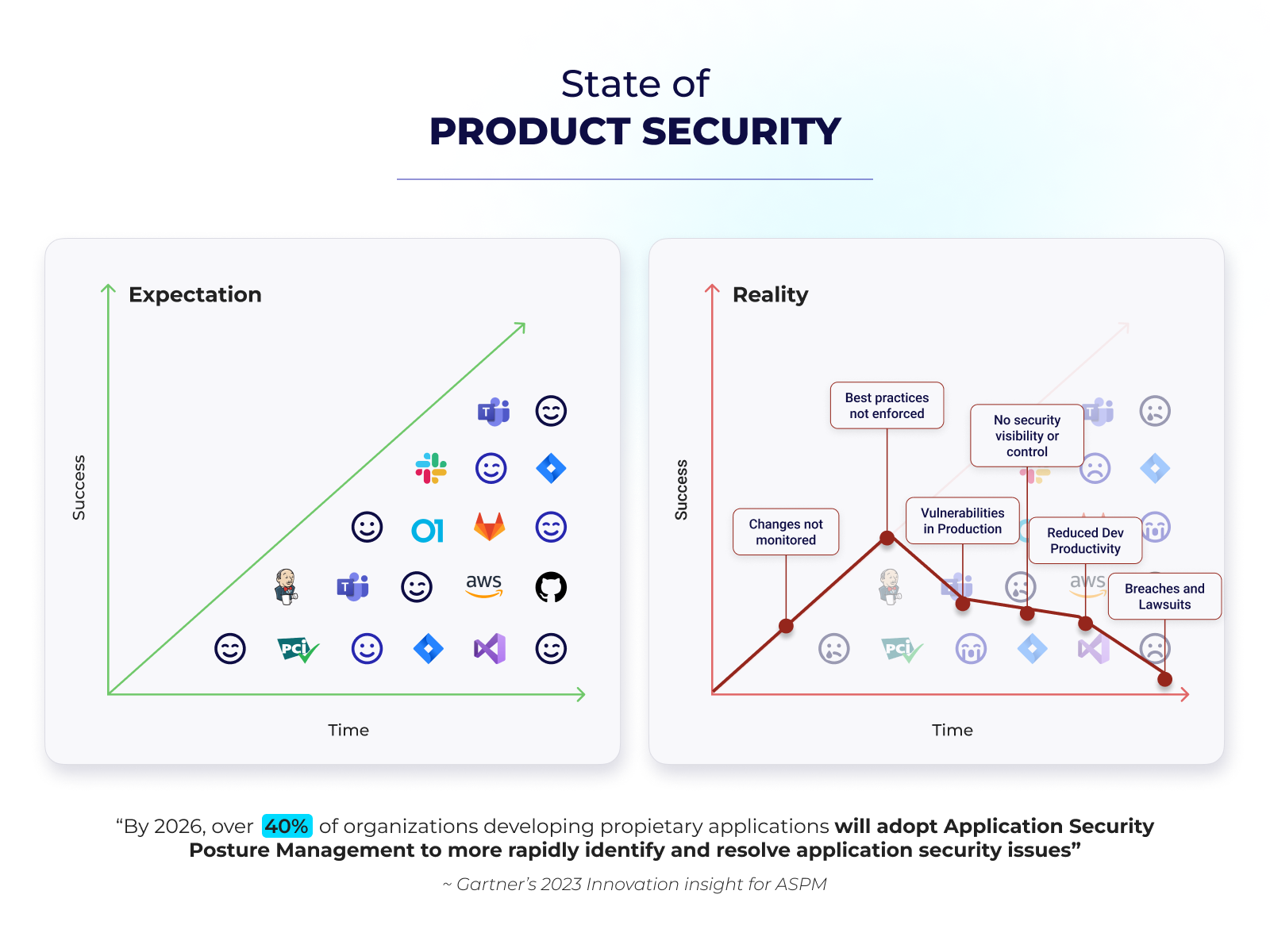
How Security by Design Saves Costs
Investing in Security by Design early delivers compounding cost-saving benefits:
- Reduced Breaches: Automating vulnerability management minimizes incidents caused by human error or misconfigurations.
- Accelerated Compliance: Built-in templates for certifications streamline audits and reduce complexity.
- Tool and Cost Optimization: Streamlined platforms reduce tool sprawl by replacing redundant tools, cutting licensing costs, and highlighting which tools deliver value for smarter investments.
- Continuous Improvement: Platforms offering ongoing education and performance tracking ensure your team evolves alongside your security needs.
- Complexity: Legacy tools drive up costs and overwhelm teams with inefficiencies, while streamlined platforms reduce waste and align with DevOps goals.
- Cuts Training Costs: Provides built-in, real-time training and upskilling, streamlining onboarding and reducing reliance on costly external courses or certifications.
Start Secure Software Development or Pay Later
For organizations developing software, embedding Security by Design is not optional—it’s essential. A strong security posture ensures compliance, reduces risk, and builds trust with customers and stakeholders.
By adopting Software security best practices and integrating Security in SDLC, you’re not just protecting your technology—you’re empowering your team and future-proofing your business.
Ready to build security into your foundation? Schedule your demo today
SHARE!
More Resources