Repo-First Thinking Is Failing Application Security—Here’s What Actually Works
Traditional Application Security Posture Management (ASPM) vendors are getting it wrong because they’re focused on the wrong unit of measure.

Most ASPM tools track risk at the repo level, assuming that’s where security teams should manage vulnerabilities. But software risk isn’t confined to a repo—it lives in how applications are architected, how teams write and review code, and how software is shipped into production.
This repo-first approach leads to fragmented insights, endless manual effort, and security findings without context—making it nearly impossible to drive meaningful risk reduction.
The Problem: Dumping Security Findings Without Context
A security leader recently posted about this frustration:
"One app can have 20 repos. One repo can have five different apps. But ASPM vendors? They treat everything as repo-first. Findings are scattered repo-wise, risks are broken down repo-wise, and security teams are left manually stitching the pieces together."
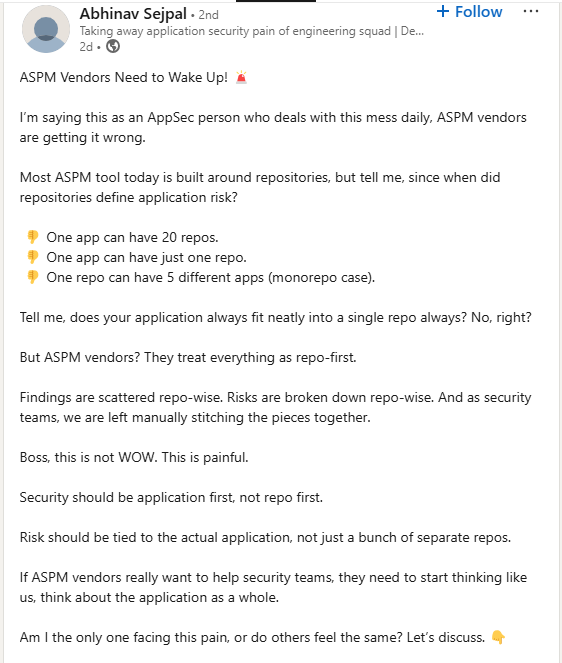
And they’re absolutely right. Security risk isn't about the repositories—it lives in how software is built, deployed, and maintained. But ASPM tools have forced security teams into a disjointed, repo-by-repo analysis that completely ignores application context. This is the core failure of the current ASPM market:
🚨
Aggregated vulnerability dumps without real context. Security teams get an overwhelming list of issues—but no clear way to prioritize what actually matters at the application or portfolio level.
🚨 Risk isn’t repo-based—it’s application-based. One repo might not equal one application, and most teams work across multiple repos. Security risk needs to be measured holistically across product lines and engineering groups.
🚨 Security teams are drowning in fragmented data. Instead of helping organizations improve their security posture, ASPM tools are forcing security teams to manually reconstruct risk across multiple repos, teams, and business units.
The result? A security posture that looks great on a slide deck but fails in execution.
We Saw This Problem Coming Long Ago—And Solved It
This isn’t a new issue. Back in 2015, while consulting on how to embed security into DevOps, we saw first-hand how broken security measurement was.
Instead of driving real security adoption, organizations were:
✅
Tracking risks but not execution. Dashboards were full of vulnerabilities, but there was
no clear way to measure how effectively teams were fixing them.
✅
Ignoring product and portfolio context.
Security was being measured in silos—not across entire applications or engineering groups.
✅
Creating friction between security and development.
Security tools slowed teams down, enforcing policies instead of
helping developers build secure software faster. Developers are overwhelmed with findings that lack actionable insight.
Then in 2024,
Microsoft started pushing for a new model, validating what we had already been building—security has to be embedded into engineering workflows and measured holistically, not just tracked at the repo level.
But we didn’t follow the trend—we defined it:
We Engineered ASPM Before It Had a Name—Then Moved Beyond It
Before Gartner even coined the ASPM category, we had already patented it. But we knew from the start: posture tracking alone wasn’t enough. That’s why we built Start Left® to go beyond ASPM and focus on how security is adopted, governed, and continuously improved.
🚀
Not just another ASPM – We go beyond posture management to optimize engineering execution.
🚀
Security that drives excellence – Align risk insights with software quality and team performance.
🚀
Patented innovation, proven results – We built the foundation for ASPM—then engineered what’s next.
The Future: Execution-Driven Security, Not Repo-First Tracking
Start Left® moves beyond repo-based ASPM and delivers context-driven risk insights, developer optimization, and execution intelligence that actually drive security adoption.
✔
Security insights with product and portfolio context – Measure risk across teams, applications, and business units—not just scattered repos.
✔
Developer optimization and upskilling – Ensure security isn’t just a policy but a core part of how engineering teams grow, learn, and execute.
✔
Execution-focused risk measurement – Move beyond tracking vulnerabilities to measuring how effectively security is adopted and applied.
The result? Security that works, without friction.
The industry doesn’t need another tool that dumps vulnerabilities without context. It needs a security execution platform that aligns risk with product, portfolio, and engineering maturity.
🔹 Security must be application-first, not repo-first.
🔹 Posture tracking is meaningless without execution.
🔹 If security slows engineers down, they won’t adopt it.
It’s time to move on from repo-first security and start optimizing how teams and individual developers actually build software.
Start Left® isn’t just another ASPM—we’re the next evolution. Let’s talk.
🚀
SHARE!
More Resources















