The Evolution Security Never Finished: From Reactive to Excellent
From Reactive to Engineering Excellence
In our original "Toyota Moment" post, we exposed the fundamental flaw in how cybersecurity has evolved: we’ve treated it like post-production inspection, not like quality engineering. This follow-up digs deeper into how we got here, why the industry's stuck in a loop, and what the shift to Execution Intelligence really means.
The security industry, much like early manufacturing, was built on reactivity—not design. But just as Toyota revolutionized manufacturing with Lean systems and embedded quality, software security is ready for its own transformation.
🔁
Here’s how it’s played out over the last 25 years:
REACTIVE
(2000-2015)
— Piling on tools, alerts, and policies
⬇
WARRANTY
(2015-2025)
— CSPM + GRC retrofits risk after code ships; shift-left emerges
⬇
PROACTIVE
(2022-2026)
— ASPM solves what CSPM misses (but only tracks and doesn't fix the overarching problems with the security "system")
⬇
EXCELLENCE
(2025-FUTURE)
— Start Left as a methodology connects risk to developer behavior and builds security into execution itself
25 Years of Backwards Security:
A Timeline of Solving Symptoms
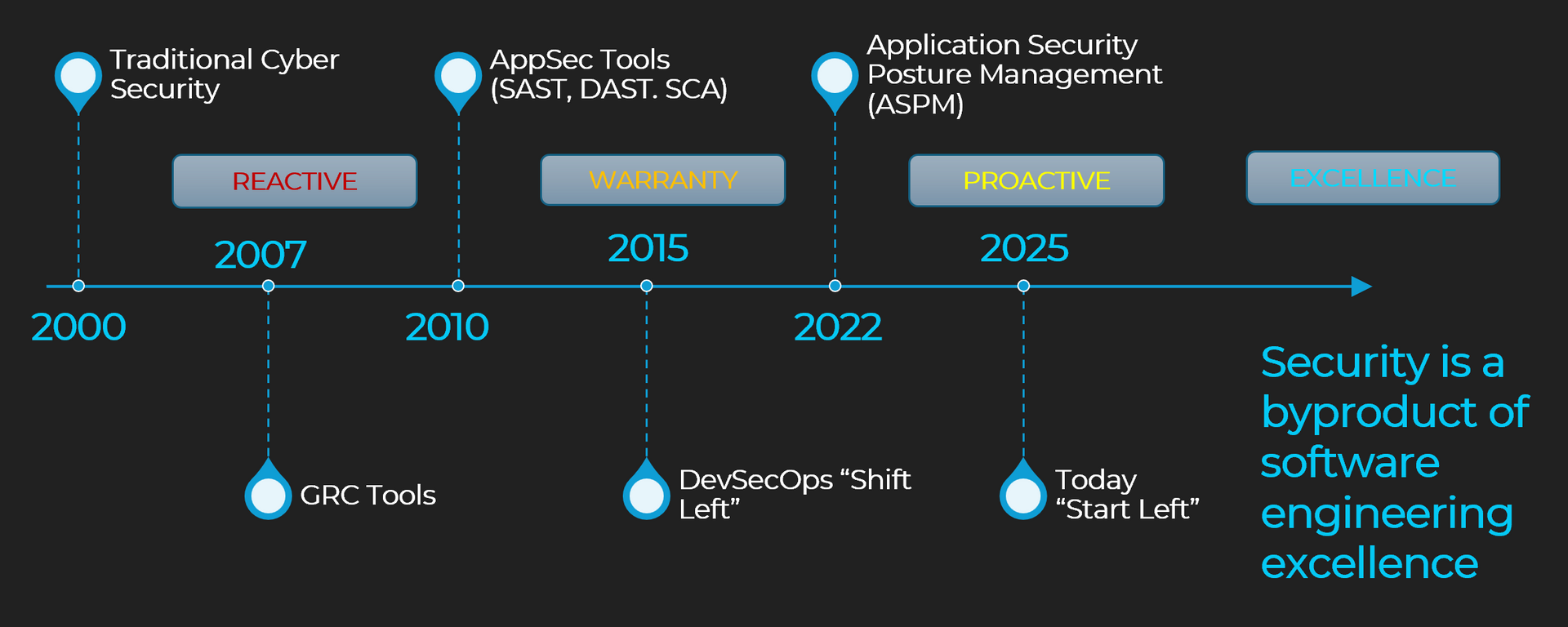
REACTIVE: The Age of Alerts & Afterthoughts
Early cybersecurity mirrored the inspection phase of a broken assembly line. Problems were found late. Fixes were manual. Security teams were siloed. Developers were an afterthought.
Security tools flooded teams with alerts. The goal was to detect, not prevent. Metrics focused on volume—vulnerabilities found, issues logged—not value or improvement.
Like the early days of manufacturing before Lean, software quality was something patched at the end—not engineered from the start.
WARRANTY: Security as Rework
As systems scaled and cloud infrastructure exploded, tools like
CSPM (cloud security posture management)
and GRC
(governance, risk, compliance)
emerged to manage post-deployment risk. But they did so like warranty work: finding issues after release, retrofitting compliance and patching in the cloud, reacting to what should’ve been built right in the first place.
This era created expensive delays, technical debt, and security that moved slower than the business.
It also mirrored
Eli Goldratt’s “The Goal”—where throughput and flow were bottlenecked by misaligned processes, not lack of effort.
Security is a constraint, not a catalyst.
PROACTIVE: The Shift-Left Awakening
ASPM (application security posture management) entered the scene to push security earlier. It gave us better visibility, mapping assets, surfacing vulnerabilities, and integrating into pipelines. But ASPM, too, became bloated with dashboards and posture tracking—without fixing the underlying problem: developer execution.
As described in "The Phoenix Project" and "The Mythical Man Month," you don’t improve outcomes by adding more people, more alerts, or more pressure. You improve the system. You empower teams. You embed quality.
And yet, ASPM stops short. It measures risk. It doesn’t reduce it.
EXCELLENCE: The Execution Intelligence Era
Start Left® introduces a new category: Execution Intelligence. It doesn't track security at the edges—it connects it to the center of where software is built: inside developer workflows, engineering systems, and team behaviors.
We:
- Correlate risk to developers, teams, and execution habits
- Guide improvement with embedded coaching, training, and upskilling
- Gamify governance to drive engagement and adoption
- Create feedback loops that accelerate quality, not rework
This aligns directly with
Microsoft’s Secure Future Initiative,
CISA’s Secure-by-Design principles, and the
Agile Manifesto itself:
build quality in from the start, and empower teams to own it.
The Flywheel Is Spinning: Why Now Matters
The ecosystem is converging toward this shift:
- Cyber insurers are demanding proof of secure development practices
- Security ratings platforms are evolving beyond surface-level signals
- Executive orders and regulations are elevating software liability
- Boards and CISOs are asking not "What’s the risk count?" but "How are we improving it?"
Execution Intelligence is the only answer that unifies:
- Developer experience
- Risk management
- Software quality
- Business velocity
From Compliance to Competitive Advantage
Just like Toyota proved quality isn’t an overhead cost but a growth driver, Start Left® proves that security can be a byproduct of excellence—not an obstacle to it.
If you're tired of patching symptoms, waiting on scans, and watching developer trust erode with every new control—this is your moment.
The future isn’t about posture. It’s about performance.
Start Left to Build Software Right.
More Resources





The Best Teams Build World-Class Software










