Starting Left in Critical Infrastructure & Manufacturing: Securing Operational Technology (OT) & Information Technology (IT)
Bridging IT & OT for Comprehensive Security
Ron Gula, founder and former CEO of Tenable, and Managing Partner of Gula Tech Adventures, released a video with an animated segment and then a discussion about "Securing Operational Technology" referencing CISA's Secure By Design and portfolio company, including Start Left® Security. Here is an longer explanation of how Start Left® aligns with CISA secure-by-design to secure OT & IT.
Overview:
In the critical infrastructure and manufacturing sectors, the convergence of Information Technology (IT) and Operational Technology (OT) environments introduces unique security challenges. Start Left® offers a comprehensive solution designed to secure both IT and OT environments, ensuring a cohesive and robust security strategy across the entire manufacturing and industrial landscape.
Value Proposition:
Start Left® empowers manufacturing and infrastructure companies by embedding AI-driven security leadership (CPSO) into both IT and OT teams, fostering a culture of security-first operations. Our platform enables organizations to achieve secure-by-design processes that protect critical assets, mitigate risks, and comply with industry regulations, ensuring the resilience of their operations.
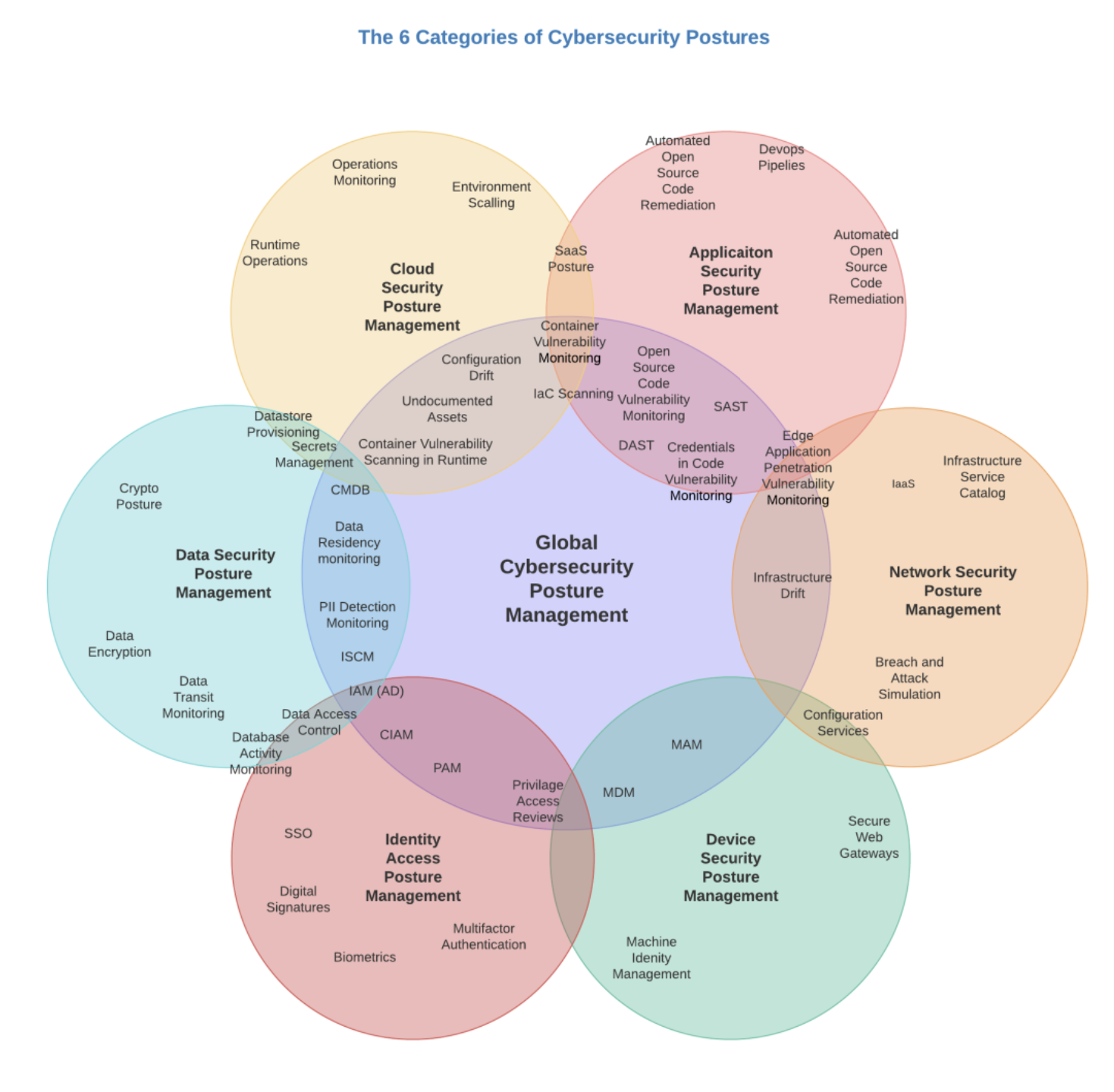
Understanding Where This Fits:
Start Left®’s Role in Enhancing Cybersecurity Postures:
- Secure By Design with Application Security Posture Management (ASPM) Platform:
- Value Prop: Start Left® ensures end-to-end product security across the application lifecycle, safeguarding software systems critical to both IT and OT environments. By integrating ASPM, we help manufacturers detect and remediate vulnerabilities in applications that control key infrastructure and processes.
- Use Case: Secure applications that manage industrial control systems (ICS) and SCADA networks to prevent disruptions caused by cyber threats.
- “Shift Everywhere” with Cloud Security Posture Management (CSPM) Integration:
- Value Prop: Start Left® offers continuous risk assessment and monitoring of cloud environments, ensuring the security of cloud infrastructure used in critical infrastructure operations. By embedding security leadership into cloud operations, we help prioritize risks and enforce security measures that align with industrial control processes.
- Use Case: Protect cloud-based platforms used for real-time data analytics in manufacturing, ensuring the confidentiality and integrity of sensitive operational data.
- Vendor Risk Management (VRM) Combining ASPM & CSPM Product Security Scoring:
- Value Prop: Start Left® integrates ASPM and CSPM into a unified Vendor Risk Management solution, enabling organizations to assess the security posture of third-party software, vendors, and outsourced developers. This ensures that all external partners meet stringent security standards, mitigating risks across the supply chain.
- Use Case: Evaluate the security practices of industrial equipment vendors and cloud infrastructure providers to ensure compliance with internal security policies, thereby preventing third-party vulnerabilities from impacting operational continuity.
Conclusion:
Start Left® provides a holistic, program-centric approach to securing both IT and OT environments in critical infrastructure and manufacturing. By aligning with key cybersecurity postures, Start Left® ensures that organizations can protect their essential assets, maintain operational continuity, and drive a security-first culture across their entire operation.
SHARE!
More Resources